Activity and Authentication Analyzer (AAAnalyzer) is the security, forensic software, now distributed as Beta, to implement the activity analysis, to counteract to such an analysis and to change the system settings and policies, to prohibit and to restrict the access to the stored sensitive to content data and available services
Monday, March 1, 2004
Твикеры
Особенностью является очень хитрая возможность поиска по реестру: может быть проведен по определенному условию, например, поиск всех ключей, отвечающих за настройку логина пользователей в системе. Для ХР это программа необходима в том случае, если у тебя нет желания искать все настройки в реестре самостоятельно.
Activity and Authentication Analyzer позволяет повысить защищенность твоей машины. Например, недавно найденный баг шестого эксплорера (возможность запуска любых приложений с твоего винта при заходе на "особую" страничку в интернете) ликвидируется этой программой простой установкой галочки в твиках осла! И таких мелочей множество.
Спецхакер 03(40) 2004
Thursday, February 20, 2003
Policies for the Windows startup management
The article describes the System Policies, which allow to manage the application startup in Windows 98/ME/2000/XP.
This article describes four system policies managing the startup lists, which contents are processed by Windows during the initial system boot. The talk will be about four lists, which values, containing the documents or applications names, are stored in the following keys:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
Here are few notes of these lists. The lists, which are located in HKEY_LOCAL_MACHINE hive, as it follows from the name, are common for all the system, and the HKEY_CURRENT_USER lists are worked through only for the current user registered in the system. The lists stored in HKEY_LOCAL_MACHINE hive are processed before the lists, stored in HKEY_CURRENT_USER hive. As it follows from the very name of key, the launch of document or application, registered in the key "RunOnce" occurs one time, notwithstanding whether the launch has been successful or not. The value stored in key "RunOnce", is deleted before the launch of application, which name it contains.
To avoid the reiteration I introduce the features common for all the policies. All the policies are applicable for Windows versions 98, ME, 2000 and XP. Their states are stored in numeric values of DWORD type. The values can be of binary type for Windows 98, ME. All the policies are of Boolean type. For the DWORD-values the value "1" stands for the active state, the value "0" blocks the policy, turning it to the disabled state. Two values "01 00 00 00" and "00 00 00 00" will represent the corresponding states of policy for the values of binary type. "By default" the policies are not enabled in the system. The missing of corresponding value in the system registry is equivalent to the disabled state of the policy. All the values must be stored in "Software\Microsoft\Windows\CurrentVersion\Policies\Explorer" key.
The values standing for the state of the policy can be in both HKEY_LOCAL_MACHINE and HKEY_CURRENT_USER hive. The value, located in HKEY_LOCAL_MACHINE hive, has an effect on the whole system, in comparison with value in HKEY_CURRENT_USER affecting the current user. If the same policy appears in both hives of the system registry, the policy, which value is in HKEY_LOCAL_MACHINE hive, has the priority over the policy with the value in HKEY_CURRENT_USER.
Disable the LOCAL MACHINE Run list
The state of this policy is stored in the "DisableLocalMachineRun" value. When the policy is in active state, the system ignores the content of "Run" list, locating in LOCAL MACHINE.
Disable the LOCAL MACHINE Run Once list
The value "DisableLocalMachineRunOnce" is responsible for the state of this policy. If the policy is in active state, the system ignores the "RunOnce" content in LOCAL MACHINE.
Disable the CURRENT USER Run list
"DisableCurrentUserRun" value represents the state of this not documented policy. This policy is directed to prohibit the system from processing the content of "Run" list, locating in the HKEY_CURRENT_USER hive of the system registry.
Disable the CURRENT USER Run Once list
Microsoft does not document this system policy either. Its state is stored in the "DisableCurrentUserRunOnce" value. When the policy is enabled, the system ignores the content of "RunOnce", storing in HKEY_CURRENT_USER.
The implementation in Activity and Authentication Analyzer
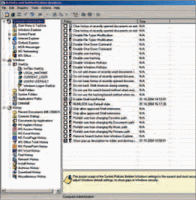
In order to see the state of above-mentioned policies or to manipulate them in Activity and Authentication Analyzer follow in the left navigation pane next way:
Computer Administration then Control Panel, then Windows StartUp and find in the right list items corresponding to these policies named:
- Disable the CURRENT USER Run list
- Disable the CURRENT USER Run Once list
- Disable the LOCAL MACHINE Run list
- Disable the LOCAL MACHINE Run Once list
Thursday, February 6, 2003
Disable Save Password in Dial-Up Connections
"By default", in Dial-Up connections the entered password is saved after successful connection, if the option "Save password", located on Dial-Up dialog box, is selected. After the password has been saved, it is not to be entered again, it is suggested automatically to corresponding edit box. The users used to have feeble memory or simply do not want to force it. For such category of users the password caching in Dial-Up connections is a definite convenience. The password caching may be the serious gap in the system security or the network security on the whole. And, under the security considerations, the administrator may wish to disable caching of the Dial-Up passwords.
The numeric DWORD-value "DisableSavePassword", which must be stored in the "SYSTEM\CurrentControlSet\Services\RasMan\Parameters" system registry key, in the HKEY_LOCAL_MACHINE hive, stands for the system policy, which while being in active state, disables the save password in Dial-Up connections. The "1" value enables the policy, "0" or missing of the value set the policy to not active state. When it is set to active state, the option "Save password" will; be hidden, and cached passwords will be lost.
And the last note: the policy is applicable in Windows NT 4, 2000, XP.
In order to see the state of above-mention policy "Disable Save Password in Dial-Up Connections" or to manipulate it in Activity and Authentication Analyzer follow in the left navigation pane next way:
Computer Administration then Control Panel, then Passwords and find it in the right list item corresponding to this policies named:
- Disable Save Password in Dial-Up Networking
Activity and Authentication Analyzer history
"Activity and Authentication Analyzer" takes into account what system policies and what histories of user activity are inherent in...